Application note
Cyber security on Vehicles: Roadmap to Compliance
New EU transportation regulations give a pragmatic approach to Cyber Security for connected vehicles.

Overview
Transportation regulations give a pragmatic approach to cyber security for connected vehicles. Approving a car or a truck for compliancy in public roads is challenging because the life of persons is taken into account. Cyber attacks
are a serious threat in this context and it’s important to understand how and to what extent regulations are dictating ways for building security.
In this white paper Bluewind will illustrate the Cyber Security on vehicle status until 2021. Starting by given a background on vehicles regulation, Bluewind will explain the context of cyber security on Vehicle. Connected Vehicles can’t ignore the safety consequences of a hack. In the end, there will be an overview to the new regulations and standards (EU Regulation No. 2019/2144). Bluewind will show the new guidelines R155, R156 and the ISO/SAE 21434.
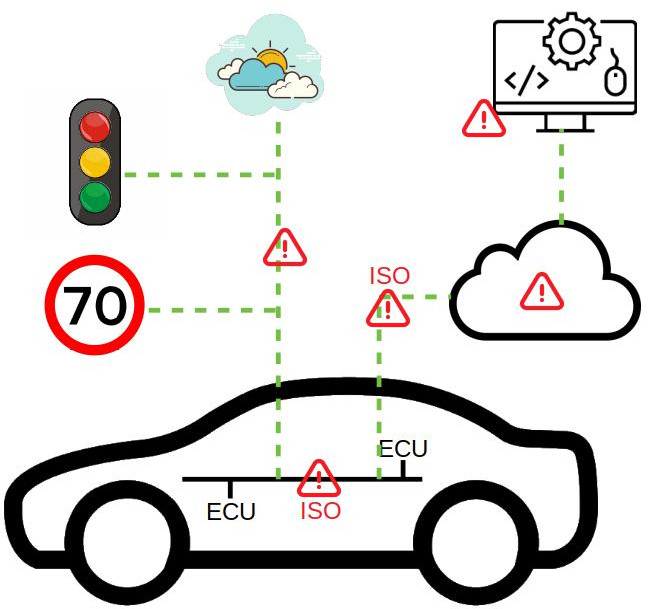
Cyber Security on Vehicles
The context of cyber security is different based on vehicles generations, components and threats. The generation of vehicles range from locally connected models to totally meshed ones.
Components relevant to cyber security are ECUs (electronic parts with software), on-board communication buses, remote communication channels and external entities like cloud services and road signals.
Threats to such components are categorized by asset, potential damage and severity. Overall, listing all possibilities is a process that resembles the safety risks and mitigating measures analysis well known to whom functional safety
is a familiar engineering practice.
New Regulations and Standards
R155 and R156 consider the full lifecycle of a vehicle from the cyber security point of view. The process and not the algorithms or implementations is taken into account, similar to Functional Safety approach. The Engineering Standards ISO 26262-2018 (functional safety), ISO/PAS 21448 (safety of the intended functionality) and ISO/SAE 21434 (cybersecurity engineering) are explicitly recalled and suggested for adoption.
Special mention goes to ISO/SAE 21434: this is the brand new approach to cybersecurity engineering for vehicles, closely resembling ISO 26262-2018 and yet to be published in its final form, but already usable.
Conclusions
Bluewind helps identifying gaps between the development process already in place and requirements of the regulations and standards. A plan for improvement can be elaborated on top of a gap analysis.
Bluewind is able to develop and adapt architectures and algorithms for cyber security, with a deep knowledge of the dedicated hardware today available on several automotive grade microprocessors and components.

