Application note
Intrusion Detection System for On-Board Vehicle Communication
Artificial Intelligence based, supervised trained networks achieve state of the art performances in classification of cyber attacks

Overview
This White Paper is based on the talk presented at ITASEC 2021, the Italian Conference on Cybersecurity on April, 9th by Tobia Fiorese (Bluewind) and Pietro Montino.
Since the introduction of many external interfaces in modern vehicles exposes users to the risk of cyber-attacks, the need of focus on security is concrete. This paper presents the development of an Intrusion Detection System (IDS) to be deployed on a CAN bus. An IDS is a component that can detect anomalies in the behaviour of the system where it is deployed.
This machine learning based solution is composed of two parts. The first includes a supervised trained neural network that is able to distinguish among different known attacks. The second includes a discriminator that has been trained exploiting the Generative Adversarial Network (GAN) paradigm, to distinguish among the attack-free situation and an anomalous situation.
Bluewind presents here a system where supervised trained networks achieve state of the art performances in classification of known attacks and unsupervised trained networks guarantee a certain level of security, helping to strengthen the system in any case where models are weak and data are poor or missing.
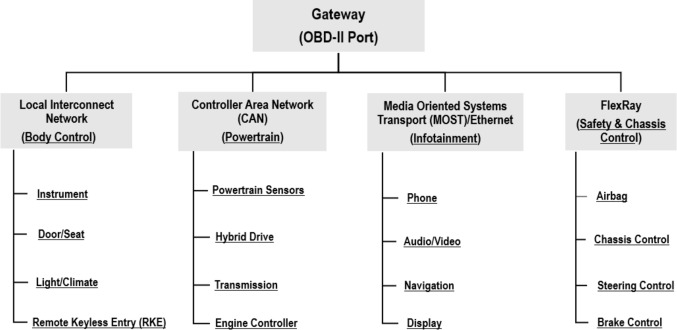
Background
In the future, each car will constantly communicate with the surrounding environment made of other cars, pedestrians and road signs giving rise to what is called the Vehicle to Everything (V2X) paradigm. In a modern vehicle there are many kinds of networks: the CAN bus is the de facto standard for safety critical applications. The CAN bus connects hundreds of Electronic Control Units (ECUs) and controls most, if not all, of the electro-mechanical actuated systems: from brakes to lights, from airbags to transmission.
In today’s connected world, finding ways to prevent cyber-attacks that could damage on-board systems and put the vehicle and the passengers at risk, has become of pivotal importance.
Solution
The input data of the proposed IDS are windows of traffic logged directly from the bus, encoded as matrices. The only features useful to identify the three attacks mentioned above turned out to be the ID of the messages in transit and the corresponding timestamps. This results in a solution that does not need to know the particular semantics of the messages transmitted by each device.
The system is composed of two subsequent networks. The first one acts as a signature based detector, and thus recognizes attacks based on previously seen examples. The second acts as an anomaly detector: in the training phase only attack-free data has been fed to the network, but still, exploiting the GAN paradigm (Generative Adversarial Network training), the result is a fairly good detection of deviations from the normal operation.
Conclusions
The proposed system uses advanced machine learning techniques to analyze raw data exchanged on CAN bus in order to detect cyber-attacks, resulting in a fairly accurate anomaly detection that is not necessarily based on knowledge of cyber threatens against the system where it may be deployed.
On November 16th our Director of Engineering Stefano Costa will host the free webinar on:
Cyber security on Vehicles: Roadmap to Compliance.

